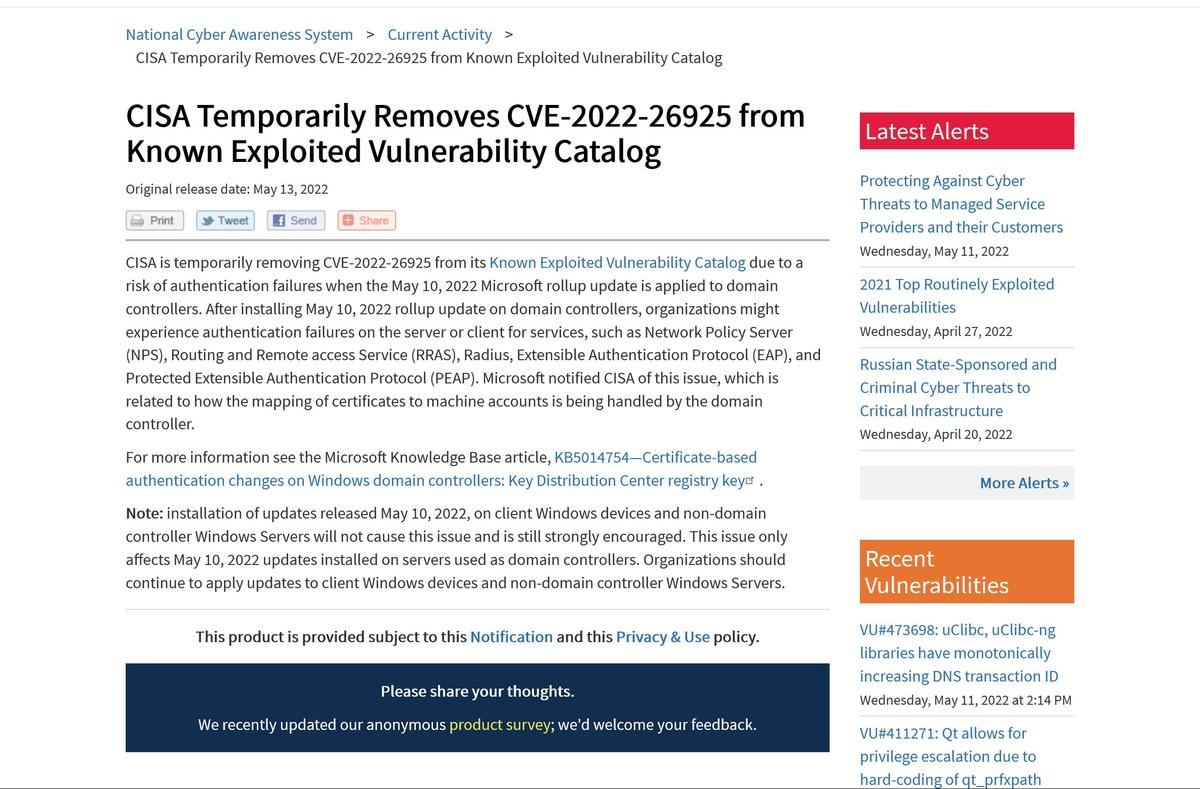
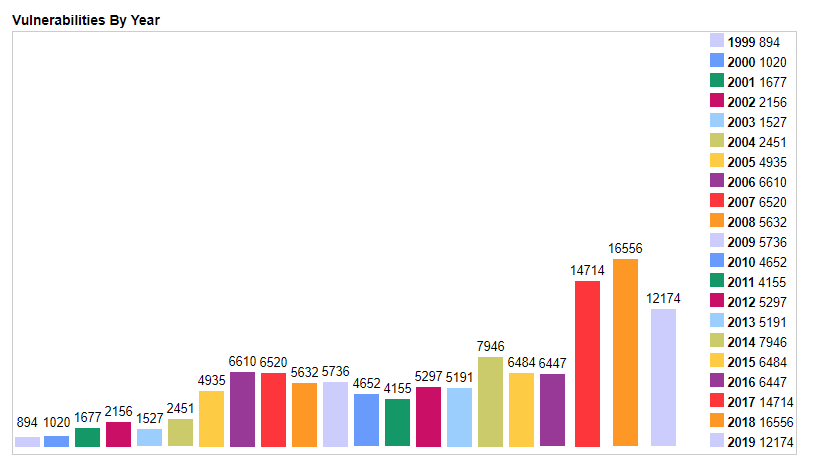
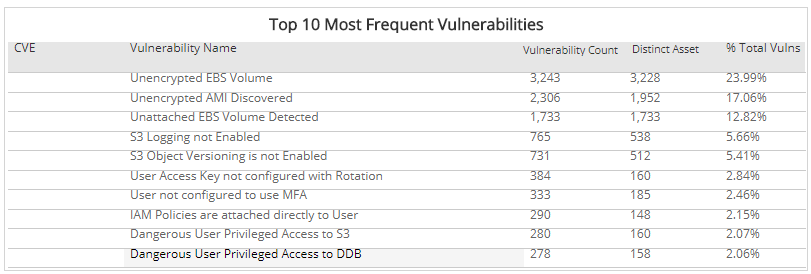
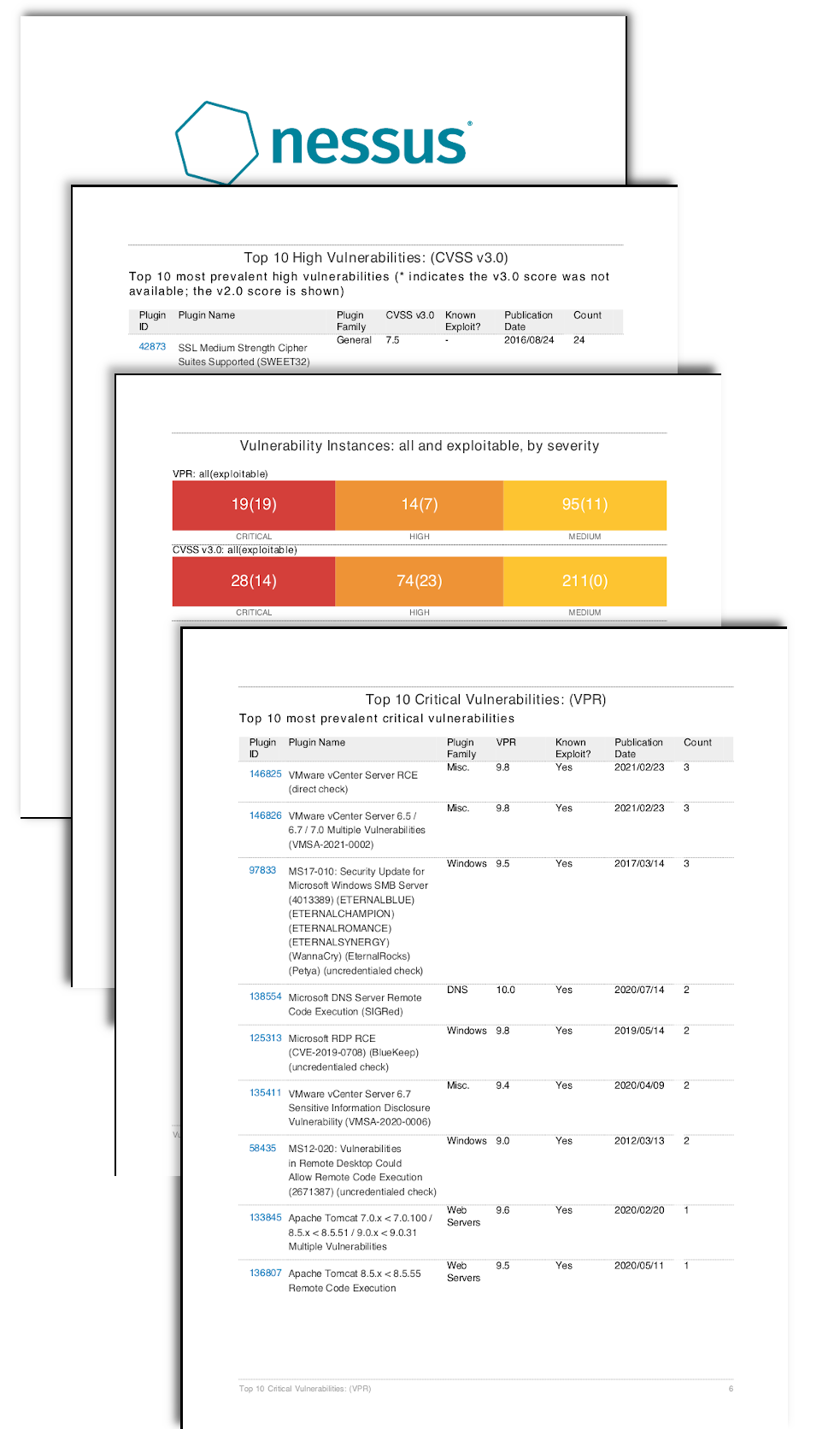
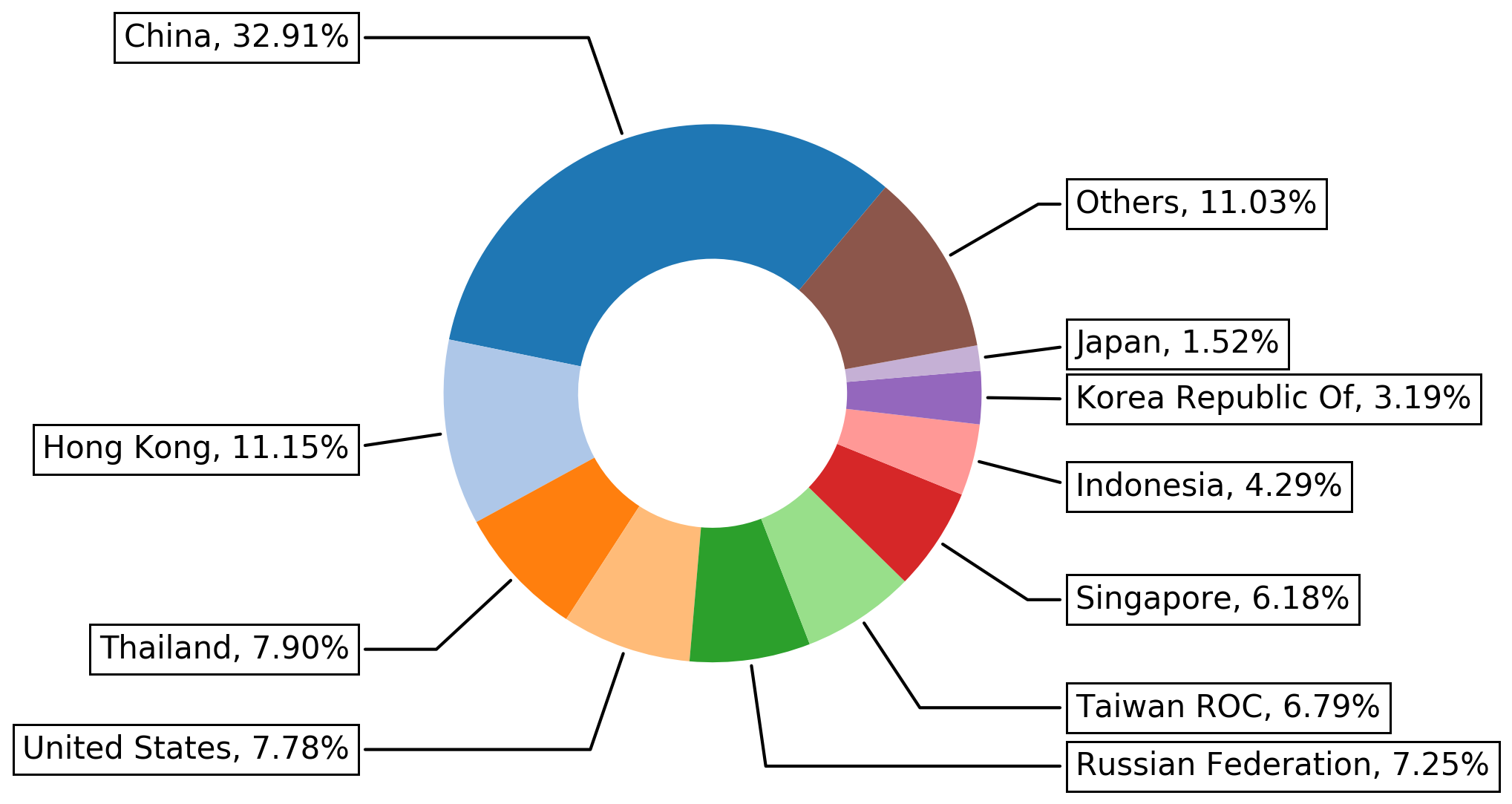
Vulnerability Scanner/Detector Log4Shell Remote Code Execution Log4j (CVE-2021–44228) — Ansible log4j-cve-2021–44228 - Ansible Pilot
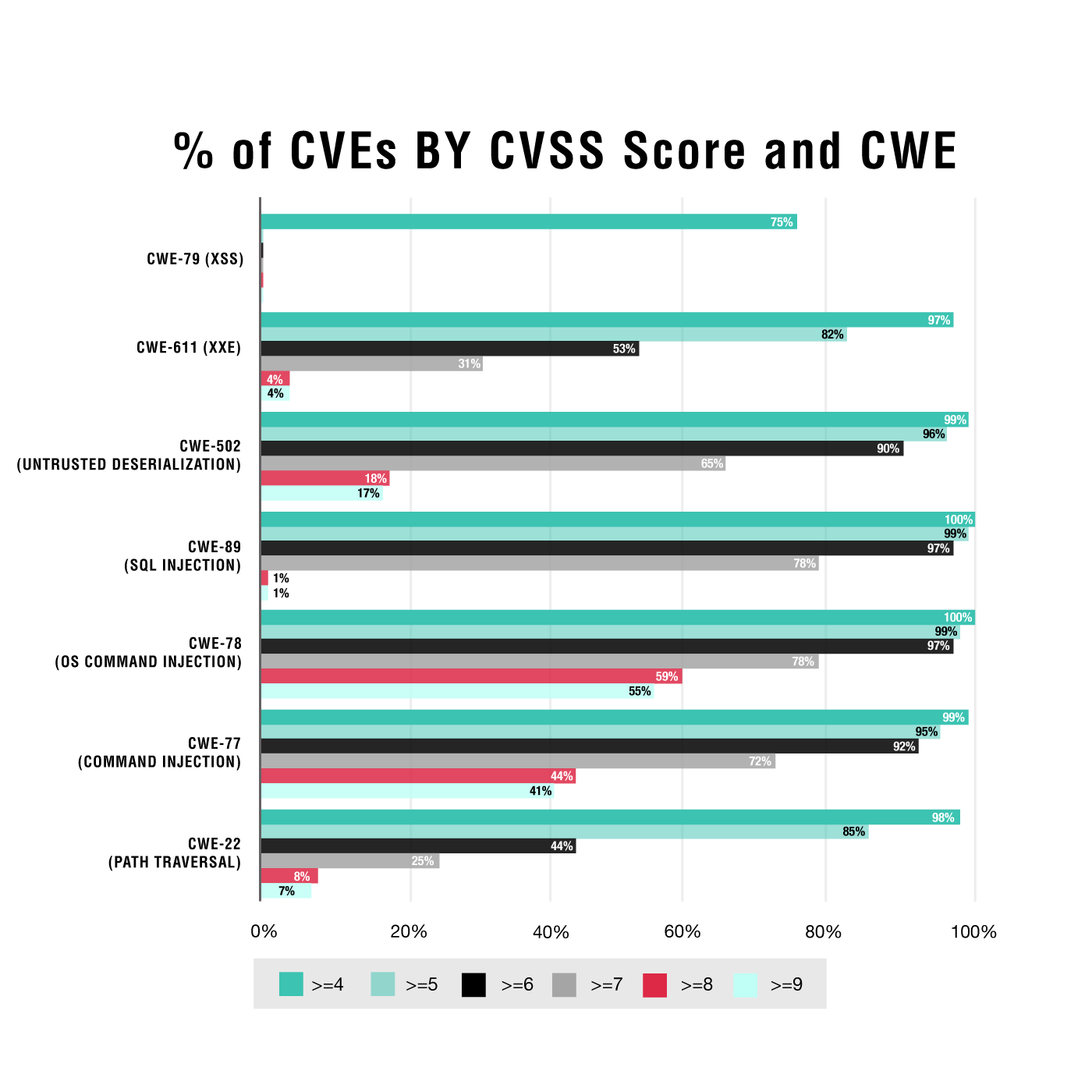
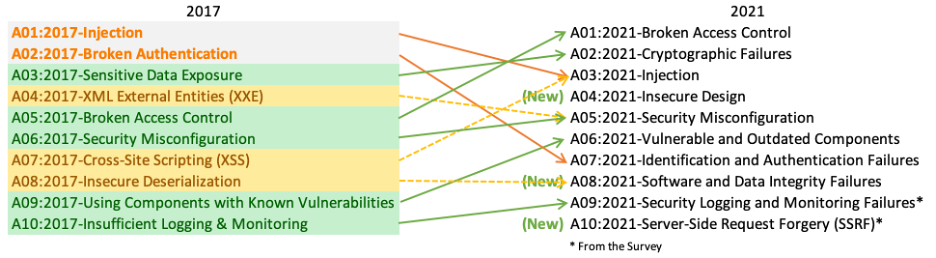
Contrast Labs: Mapping Risk Profiles for Select OWASP Top 10 Vulnerabilities to Understand Their AppSec Risk

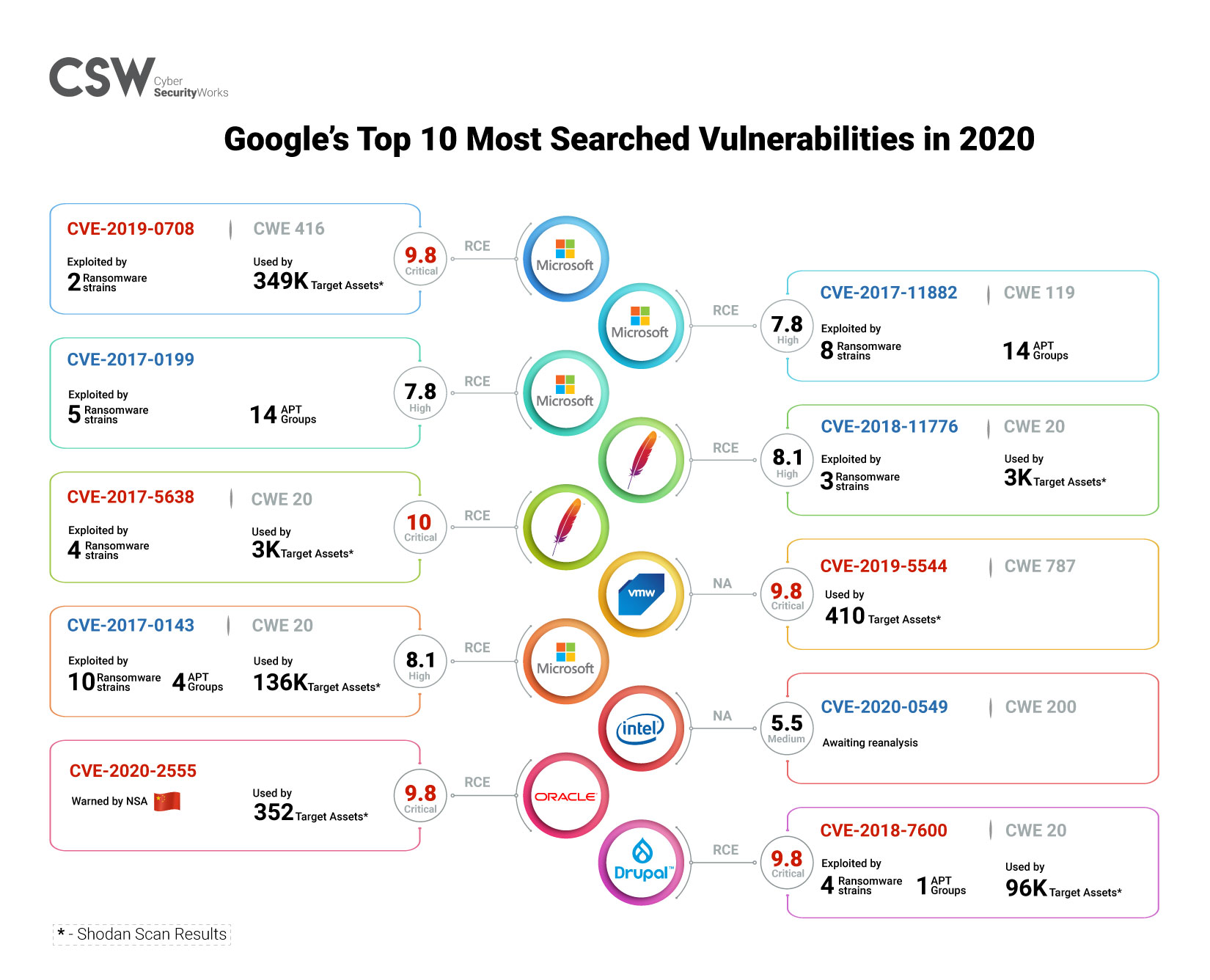
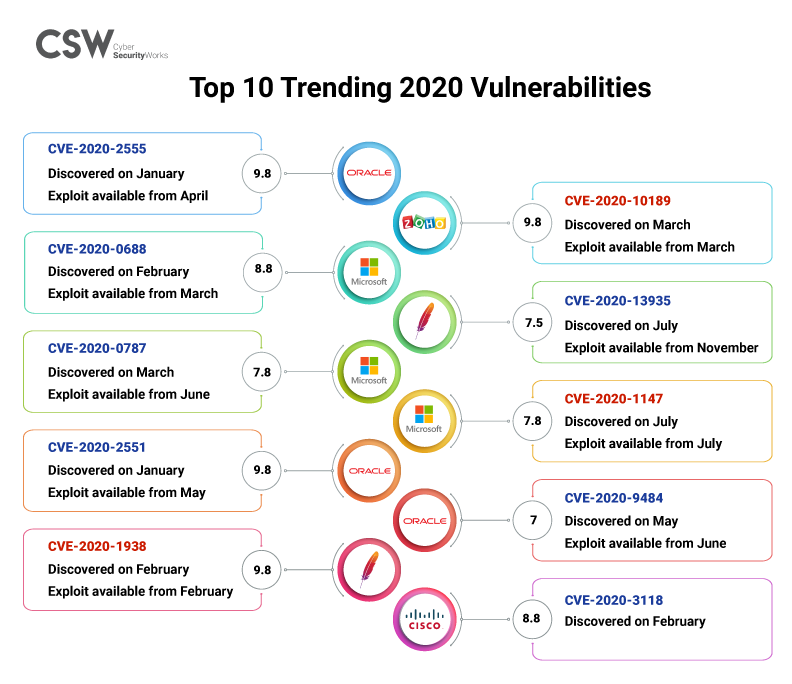
Cybersecurity Insights-5 - NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.